
Earlier this year, a new phishing campaign emerged, targeting toll roads systems across the United States, including EZDriveMA (Massachusetts), TheTollRoads (FasTrak (California)), E-ZPass NY, SunPass (Florida), E-ZPass and etc.
Unfortunately, we identified this campaign with a two-week delay. However, since Jan 22, we have actively monitored and tracked the campaign, identifying and listing over 10,000 domains so far.
This toll phishing campaign closely resembles the Postal phishing campaign we analyzed earlier. The coding structure, domain patterns, and attack methods are nearly identical. Our investigation reveals that this campaign primarily distributes phishing messages via Apple’s iMessage, sending them in high volumes to potential victims.
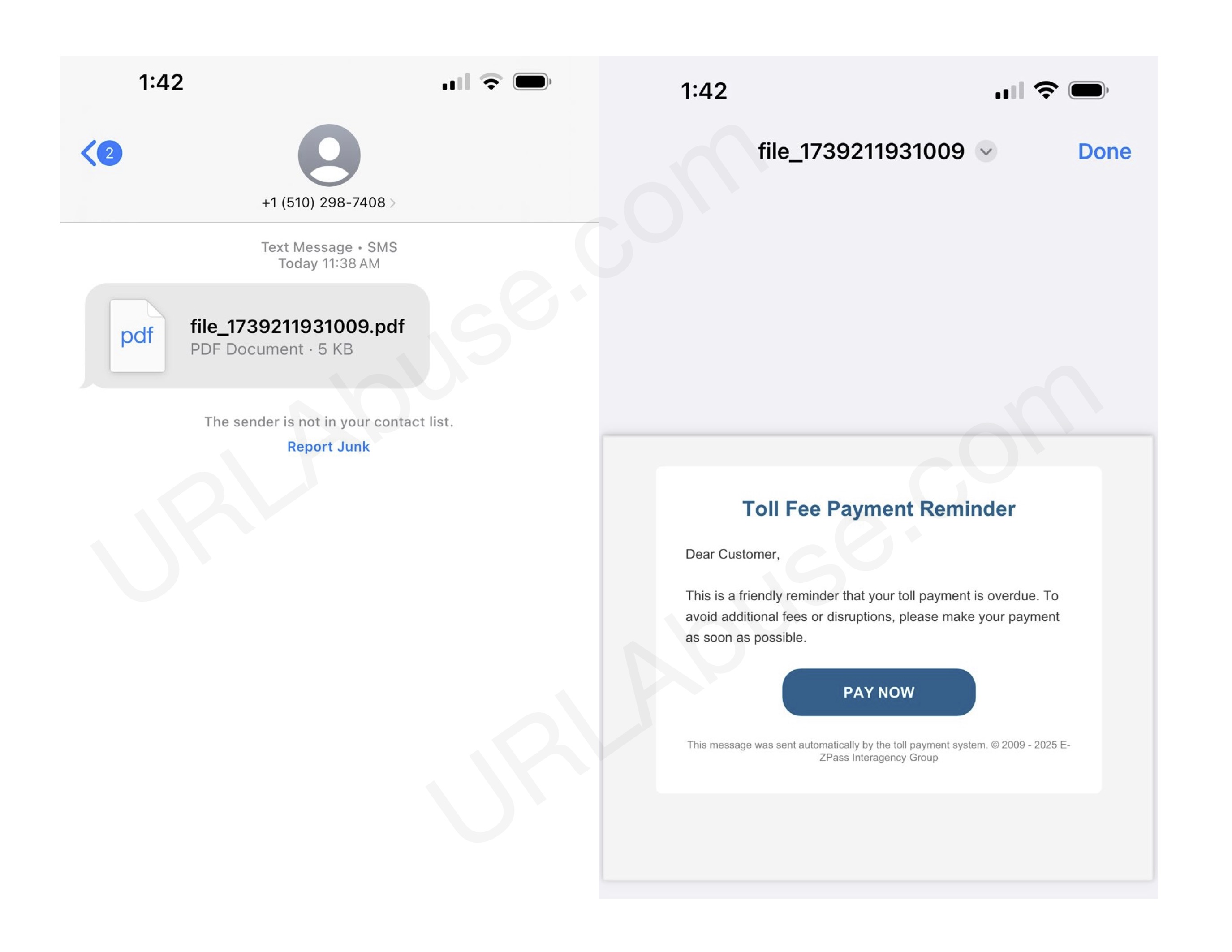
Below is an example of a phishing message sent to targets:

In the past few days, we have observed messages being sent through U.S. telecommunications carriers to victims. These messages, delivered via SMS (MMS) by cybercriminals, contain a PDF file with an embedded phishing link. When the victim clicks the ‘PAY NOW’ button inside the PDF, they are redirected to a phishing page.
ALSO SEE: An overview of the world's largest postal services phishing campaign
Campaign Analysis So Far
To date, we have identified around 10,000 domains associated with this campaign. As shown in the table below, the toll system most affected by this phishing wave is EZDriveMA (Massachusetts), followed by TheTollRoads.
| # | Target | % |
|---|---|---|
| 1 | EZDriveMA | 82.4% |
| 2 | thetollroads | 10.4% |
| 3 | E-ZPass NY | 3.6% |
| 4 | SunPass | 3.3% |
| 5 | E-ZPass | 0.2% |
| 6 | E-ZPass NJ | 0.1% |
TLDs Used in the Campaign
As expected, “.top” continues to be the most frequently used TLD in this campaign (as the name suggests). The second most used TLD is “.xin”, followed by “.vip” in third place.
| # | TLD | % of domain name registrations |
|---|---|---|
| 1 | .top | 62.6% |
| 2 | .xin | 28.5% |
| 3 | .vip | 4% |
| 4 | .sbs | 2.8% |
| 5 | .live | 1% |
| 6 | others | 1.1% |
Also see: ICANN Issued Breach Notice to .TOP Registry After URLAbuse Complaint
Registrar Insights:
It comes as no surprise that Alibaba Registrar (IANA ID: 3775) has the highest number of phishing domain registrations, leading the list by a large margin. Following closely are NameSilo, LLC (IANA ID: 1479) and Gname.com (IANA ID: 1923).
| # | Registrar | IANA ID | % Registration |
|---|---|---|---|
| 1 | Dominet (HK) Limited (ALIBABA.COM) | 3775 | 82.1% |
| 2 | NameSilo, LLC | 1479 | 9.1% |
| 3 | Gname.com Pte. Ltd | 1923 | 6.4% |
| 4 | Hefei Juming Network Technology Co., Ltd (jumi.com) | 3758 | 2.2% |
| 5 | Alibaba Cloud Computing Ltd. d/b/a HiChina (www.net.cn) | 1599 | 0.1% |
| 5 | Others | - | 0.1% |
In terms of hosting infrastructure, we found that, just like the postal campaign, most phishing domains are hosted under AS 132203 - Tencent Building, Kejizhongyi Avenue.
| # | AS | ASN | % hosted |
|---|---|---|---|
| 1 | TENCENT-NET-AP-CN Tencent Building | 132203 | 60.4% |
| 2 | CLOUDFLARENET | 13335 | 27.1% |
| 3 | ALIBABA-CN-NET Alibaba US Technology Co. | 45102 | 10.8% |
| 4 | SEDO-AS - SEDO GmbH | 47846 | 1.1% |
| 5 | PONYNET | 53667 | 0.3% |
| 6 | BAXET-GROUP | 398343 | 0.2% |
| 7 | SARNICA-AS - Sarnica-Net LTD | 48584 | 0.1% |
By notifying the relevant registries and registrars, we successfully take down approximately 80% of the identified domains this campaign.
URLAbuse continues to track this phishing campaign and notify relevant registries and registrars, providing all actionable evidence for swift takedown efforts. Our full dataset is publicly available on our feed, updated every 5 minutes. We also actively share this intelligence with our partners to strengthen response efforts.
This article is not complete, and we will update it in the future.
For any inquiries, please contact us at team[at]urlabuse.com.

Add new comment